Top of Page
- Links to move inside this page.
- HOME
- Sustainability
- Material issue 2: Basic approach
- Maintaining security and privacy
Maintaining security and privacy
The security that IIJ provides
In today's advanced information society, ensuring information security is an essential issue that cannot be ignored. As a leading provider of the Internet, an infrastructure that supports daily life, IIJ recognizes the importance of this issue and offers optimal security-related services based on our wealth of expertise and capabilities cultivated as an ISP. We are working toward a world in which the protection of every Internet user's privacy and security is the norm.
wizSafe, a brand that collectively refers to IIJ's security initiatives, signifies our stance of delivering Safety (Safe) on the Internet along With (wiz=with) users, applying the wisdom (wiz=wisdom) of experienced engineers (wiz=wizards).
Under the wizSafe brand, IIJ offers multi-point security, or a combination of multiple security measures, and contributes to increasing the security level of corporate networks with highly effective security strategies to protect customers' systems from a range of external and internal threats.

High quality security service
IIJ proposes the optimal security measures for its customers from the perspective of integrated operations based on the high level of technological and comprehensive capabilities we have cultivated as an ISP.
We provide multi-point security that combines multiple measures to protect customer systems from various external and internal threats.
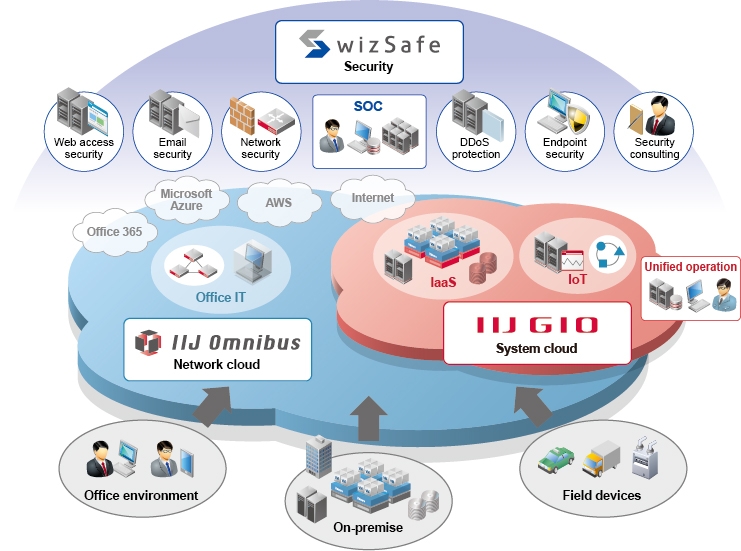
Operational structure that ensures high security
Security Operations Center (SOC) that protects customers' networks
IIJ operates the Security Operations Center (SOC), a facility that takes advantage of our expertise in security that we have developed over many years. The SOC responds to security incidents that occur on customers' IT systems by combining automatic monitoring with big data and advanced risk analyses conducted by analysts.

Privacy protection initiatives
Provide help with complying with local privacy protection regulations around the world
The latest IT, such as AI that is handling enormous volumes of data that more and more frequently contains personal information. In addition, society is requiring more privacy-conscious information handling than ever, including how to deal with the cookies used for tracking web browsing history.
An increasing number of countries, such as the US, China, Thailand, Vietnam, and Singapore, have implemented privacy protection regulations along with strict penal provisions that mirror the European Union's (EU) General Data Protection Regulation (GDPR) implemented in May 2018. In 2020, the "Amendment Act of the Act on the Protection of Personal Information, etc." will be promulgated in Japan, and enforced in April 1, 2022.
IIJ offers consulting services to help protect personal data in manner that complies with the regulations of each country and to support you in conducting business safely. In addition, we also provide specialist support with our Data Protection Officer, EU Representative Outsourcing Services for GDPR, and Incident Management and Support Service to mitigate the risks of financial penalties and reputational harm.
Knowledge sharing
Security information distribution
IIJ publishes news on our official blog and regularly publishes technical reports to share knowledge and expertise acquired through our daily service operations and research activities.

Participation in industry associations

As a member of various security-related associations, IIJ contributes to improving Japan's overall security capabilities through incident (*) information sharing, discussion, and responses of incident (*), and human resource development.
- (*)Incident: events such as virus infections and information leaks that could lead to serious accidents.
Support for developing security experts
Cyber investigator training support
To help with cybercrime investigations and prevention activities in our capacity as Internet security experts, IIJ cooperates with the police by sharing expertise and training investigators.
Providing a training course at the international conference
IIJ's security engineer team has served as lecturers at Black Hat USA.
IIJ Security Training School, Security Education Program
Engineers specializing in security pass on their advanced knowledge and skills, based on findings from their jobs which usually entail operating a security service and addressing sudden incidents while keeping an eye on the latest trends of cyberthreats. Mainly targeting security personnel of corporate information system divisions and personnel from CSIRT divisions, IIJ provides an extensive program encompassing basic and practical knowledge and supports the development of security specialists, who are in seriously short supply.
Some courses in the educational program are certified as special courses for registered information security specialists, which is positioned by the Minister of Economy, Trade and Industry as a specific course organized by private businesses and similar.
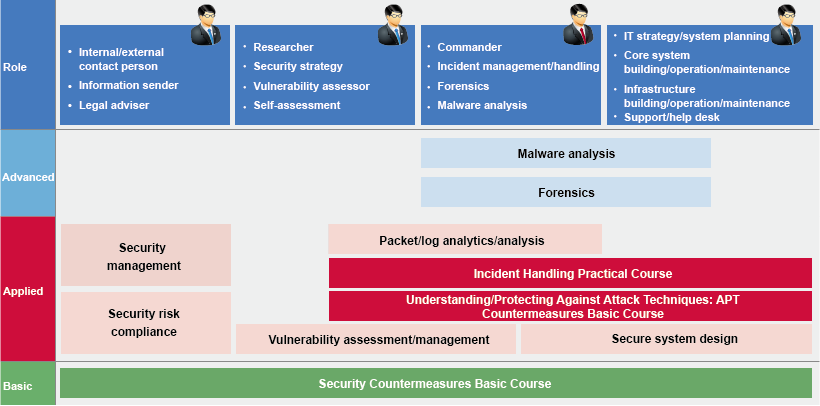
IIJ's information security governance
Information security management structure

We recognize information security governance as a crucial responsibility. This commitment to security covers protection of all sorts of entrusted information, such as customers' personal information, and our own information assets from various threats, and ensures proper security management that considers personal information protection and privacy.
Based on this idea, IIJ has set out the Basic Information Security Policy so that all our employees can conduct tasks ethically, and has built an information security management structure designed to ensure continuous improvement of our security level. In addition, we have established a conference body related to information security and personal information protection who share information throughout the company.
To instill awareness of information security in our employees, IIJ provides all employees with annual in-house training on information security and personal information protection, and also trains new graduates and mid-career employees when they join the company. Adding to these in-house information security programs, we are also driving an initiative to obtain certifications such as ISO/IEC 27017:2015, an international security standard for cloud services as well as other standards related to what we do. This ensures our customers can use our services with peace of mind.
Countermeasures against cyberattacks
IIJ is working on countermeasures against increasingly advanced and sophisticated cyberattacks, such as unauthorized access from the outside and targeted attacks. Specifically, our in-house incident response team collects threat intelligence as needed, and our own security services and specially developed and built system detect, quarantine, and deal with cyberattacks.
Compliance with the EU General Data Protection Regulation (GDPR)
To comply with the General Data Protection Regulation (GDPR) enacted by the EU in April 2016, IIJ quickly submitted our Binding Corporate Rules (BCR), which comprises documentation on information management rules unified across the IIJ Group, to the relevant supervising authority in the UK in October 2016. And IIJ Group received approval for its BCRs, on August 5, 2021. With this approval, we can process EU personal data without overly impacting customers and can transfer personal data outside the EU.
Certification under APEC Cross-Border Privacy Rules (CBPR) System
The APEC CBPR certification is a system that certifies compliance with the Asia Pacific Economic Cooperation (APEC) Privacy principles in connection with cross-border personal information protection.
APEC CBPR certification enables IIJ to be recognized as an organization protecting personal information appropriately and allows the customers using our cloud computing services and other IIJ services to transfer personal data smoothly with legal security in the APEC region (participants in CBPR: United States, Canada, Mexico, South Korea, Taiwan, Singapore, the Philippines, Australia and Japan).
ISMS certification

In April 2007, IIJ was certified by the information security management system (ISMS) compliance assessment scheme. From that year onwards, the company has been certified in additional areas every year. Going forward, we will continue to improve our information security management system to allow customers to use our services with the greatest confidence and peace of mind.
Acquiring the privacy mark
IIJ has set out a privacy protection policy to ensure appropriate acquisition, use, and provision of personal information, and we are ensuring that our employees strictly follow it. To protect personal information more effectively, we have built and been operating a personal information protection management system compliant with the JISQ15001 standard, with the privacy mark acquired. Going forward, we shall continue to improve our personal information protection management system in compliance with laws, national guidelines and other rules related to personal information.
The Information System Security Management and Assessment Program (ISMAP)
ISMAP is a program designed to have cloud services assessed and registered in advance as meeting the security requirements of the Japanese government so as to ensure a level of security and facilitate smooth introduction in government procurement of cloud services.
IIJ has various cloud services registered with ISMAP, including "IJ GIO Infrastructure P2".
- IIJ's services meet the government's security requirements (Japanese text only)
- Related Contents
End of the page.

