Innovating Security Operations Center
About IIJ SOCTop of Page
- Links to move inside this page.
- HOME
- The Security Brand "wizSafe"
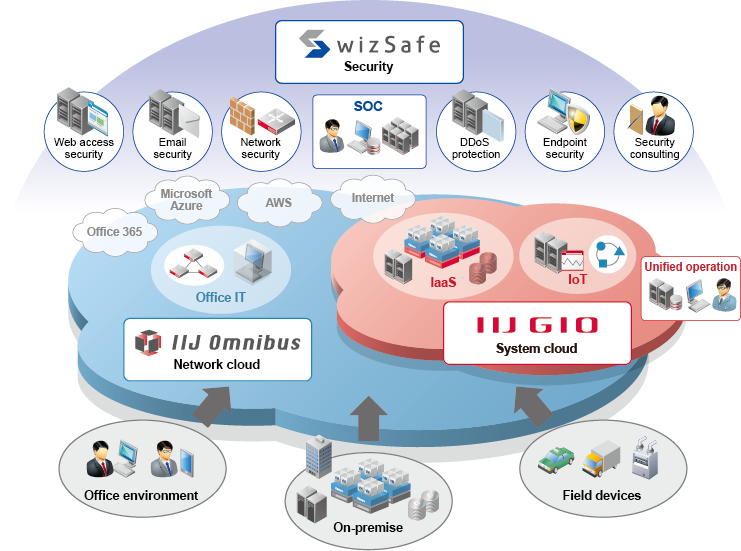
The Security Provided by wizSafe
We provide optimal security measures to customers in terms of integrated operation via SOC,
from cloud solutions to access lines and endpoints.
Multi point security
With the comprehensive strength and technical prowess that we have developed as an ISP, we provide customers with optimal security protections in terms of unified operations using SOC. In order to protect our customers' systems from a variety of threats, both internal and external, we suggest multi-point security, which combines multiple countermeasures. This effective high-security plan helps bring our customers' security to higher levels.
Security Operation Center(SOC)
We perform big data analysis based on information that is unique to ISP, such as a huge amount of logs of security equipment, backbone traffic, and DNS queries gathered by the Data Analytics Platform, and external information. From the results of analysis and the expertise of the security analysts, the SOC continues to defend customers from various threats through incident detection and notification, initial response, solution proposals, and even the implementation of countermeasures regarding IIJ operated equipment.
Chosen for Reliability and Performance
Since offering the first firewall service in Japan in 1994,
IIJ's security services have been selected by many customers covering all industry types and scales.
Our performance in Japan overwhelms the competition

- Cloud-based email security
-
IIJ Secure MX Service

No. of subscriber accounts
About2.9million
(as of Mar 31,2024)Share of Mail Security Services Market
No.1(*1)

- Cloud-based Web security
-
IIJ Secure Web Gateway Service

No. of subscriber accounts
About1.2million
(as of Mar 31,2024)Share of Web Security Services Market
No.1(*2)
(*1)Source:ITR,ITR Market View:Cyber Security Countermeasure Market 2023:
Integrated Mail Security Market:Market shares of vendor sales in FY2020-2022 (Forecast)
(*2)Source:ITR,ITR Market View:SOC Services Countermeasure for Gateway Security Market 2023:
Web Security Operation and Monitoring Services Market:Market shares of vendor sales in FY2021-2023 (Forecast)
End of the page.


 wizSafe Brand Top
wizSafe Brand Top
