
Top of Page
- Links to move inside this page.
- HOME
- The Security Brand "wizSafe"
- About IIJ SOC

Innovating Security Operations Center
IIJ's SOC is a facility that brings together the security business expertise we have developed over many years to detect and handle risks quickly and accurately by analyzing vast quantities of information.

Operations Room
A space for carrying out security operations that was designed exclusively for strict security management and the stable monitoring of customer security. Here we reference threat information, attack trends, and reputations based on the extensive logs we have access to as an ISP to implement superior attack detection and notification/handling.

Security Lab
An analysis room for handling information that poses a high security risk, including the analysis of unknown malware and forensic investigations. An expert engineer with proven skills will investigate after the data (evidence) from the devices being investigated such as PCs, servers, external HDDs, USB memory, etc., is preserved and copied.
Human Resource Development
At IIJ, we are devoted to developing human resources with a high level of technical expertise and knowledge regarding security both inside and outside of the company.
Training of Security Analysts
At IIJ, we train human resources with the ability to perform advanced security operations.
Contributions to Security Staff Development
We actively take part in external seminar as guest lecturer, and also offer internships for students.
- Mauritius 2016 FIRST Technical Colloquium
- Security Camp 2014/2016/2017
- Blackhat Asia 2014
- Blackhat USA 2013
- Blackhat Europe 2012
- Lisbon 2013 FIRST Technical Colloquium
- Kyoto 2012 FIRST Technical Colloquium
- MWS Cup 2012
and many others

Internships for students
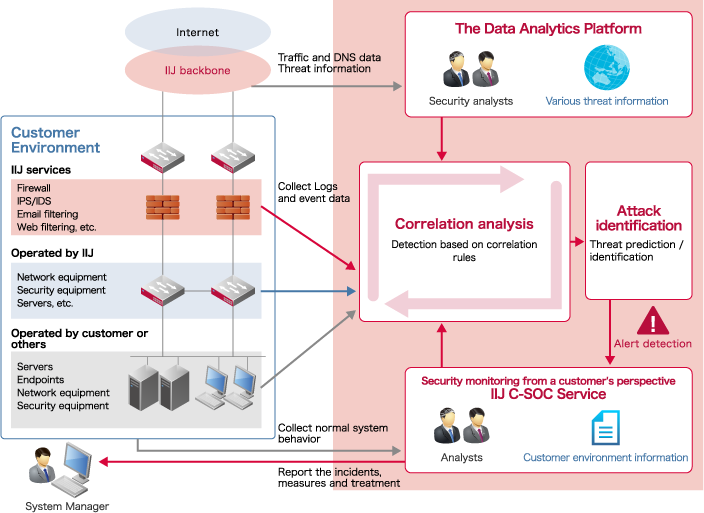
The Data Analytics Platform
At IIJ's security operations center (SOC), we integrate logs collected for each customer with IIJ's threat information. We perform everything from incident detection to notification/handling, proposal of countermeasures, and measures for equipment operated by IIJ based on the results of analysis and the knowledge of security analysts.
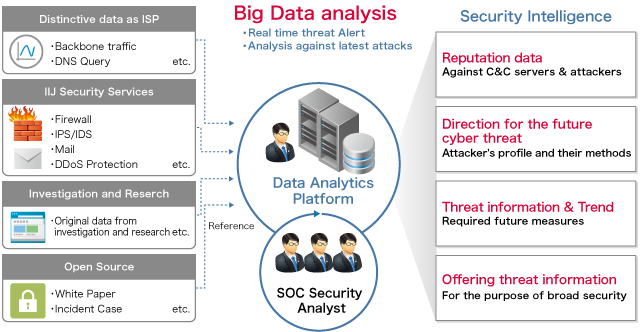
Generating security intelligence through analysis of
vast quantities of data
We accumulate our original security intelligence by analyzing data such as the logs for the massive number of security devices IIJ manages, backbone traffic, and DNS queries, along with additional external information. We use this to deal with the security incidents of customers.
End of the page.

 wizSafe Brand Top
wizSafe Brand Top
