Top of Page
- Links to move inside this page.
IIJ Change Detection and Recovery solution
About the Solution Overview
The IIJ Change Detection and Recovery solution detects website tampering threats accurately, and performs automatic recovery rapidly. This provides instantaneous detection and instantaneous recovery 24/7. We help customers operate safe and secure websites.
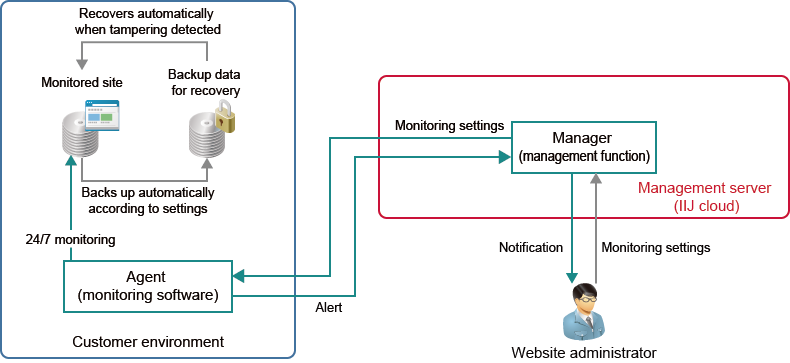
Solution Features
Instantaneous Detection/Instantaneous Recovery via Constant Monitoring for Tampering
We position Agent (monitoring software) in the customer environment. The system activates as soon as an OS event such as a file change, addition, or deletion occurs. The system can perform detection and recovery instantaneously within 0.1 seconds. Since the system remains in the stand-by condition until activated, it usually takes up a small CPU load of less than 1%.
Management Server Provided on Cloud
We provide the management server with the Manager function via the cloud. This eliminates the work required for preparing, operating, and maintaining a management server.
Preservation of Evidence for Unauthorized Uploads
The recovery/preservation mode enables preservation of evidence about the upload destination and type of file in the attempted upload.
(Japanese text only)
- Related Contents
End of the page.
