Top of Page
- Links to move inside this page.
IIJ Managed WAF Service
About the Service Overview
The IIJ Managed WAF Service detects and protects against attacks that exploit various Web system vulnerabilities with a high-performance WAF engine. This cloud-based WAF service is operated by IIJ security engineers and can be deployed for a wide range of Web systems.
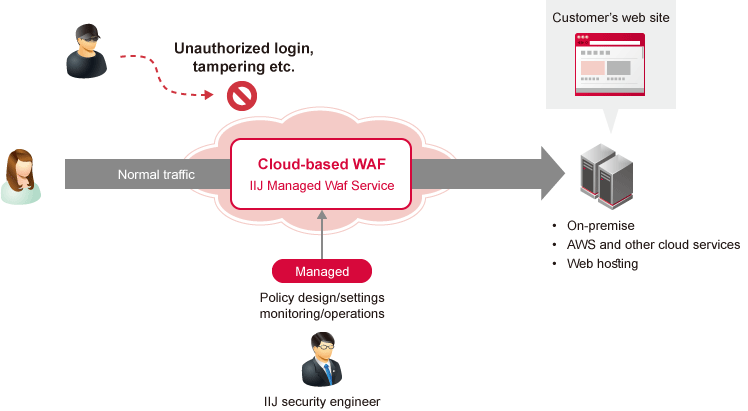
Service Features
A Managed Service Making it Possible to Deploy Truly Effective WAF
In order to provide the optimal policy for each customer's web site, we provide aging of detection rules at the time of deployment as a standard service. By performing appropriate aging in advance, misdetection can be prevented after the start of operation.
Detailed Settings Optimal for Ecommerce Sites or Sites that Handle Personal Information
Signatures and detection settings can be tuned for each site, making it optimal for sites that require high security. The service can also handle unauthorized login attacks such as brute force that threatens EC sites. Because the service has acquired cloud security authentication (ISO/IEC 27017:2015) and has been registered in the "Information Security Service Standard Compliant Service List", you can use it with confidence.
Cloud-based for Simple Deployment and Configuration Suitable for the Customer's System
Since it is cloud-based, there is no need to make major changes to the customer's system configuration. Deployment is possible by simply changing the DNS record. Also, since the system configuration is flexible, it can support a wide range of configurations, from cost-oriented simple configurations to availability-oriented redundant and DR configurations.
Detection of and Protection against DDoS Attacks in the IIJ Backbone
Decentralized anti-DDoS attack systems are deployed within the IIJ Backbone, both inside and outside the country. Large-scale DDoS attacks can be addressed by protections at the facility closest to the source of attacks. The WAF can detect attacks on each website, even those using encrypted traffic (HTTPS), and can protect them from the attacks.
(Japanese text only)
- Related Contents
End of the page.
