Top of Page
- Links to move inside this page.
IIJ EMM Utilization Support Solution for Microsoft
About the Solution Overview
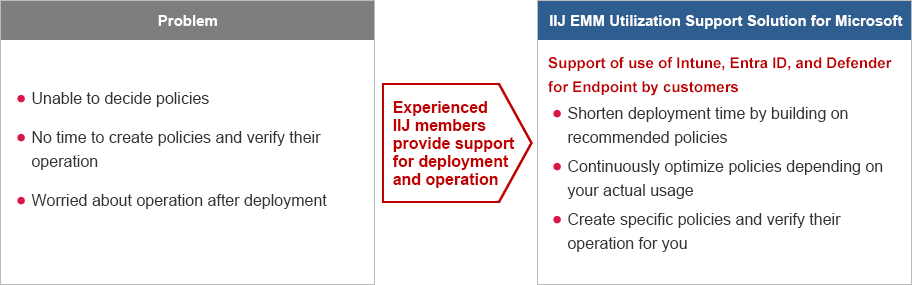
IIJ EMM Utilization Support Solution for Microsoft is a solution that examines, creates, and verifies the operation of policies that will become an issue when Microsoft Intune and Defender for Endpoint are implemented and operated. With its extensive experience in implementing and operating Microsoft 365, IIJ greatly reduces the burden on customers and makes end device management and EDR operations easier in the era of hybrid work.
Solution Features
IIJ's own recommended policies for easy implementation in Microsoft Intune
Based on the security baselines defined by Microsoft, IIJ creates its own recommended policies based on IIJ's wealth of knowledge gained from the implementation of Microsoft 365. They are provided in a form that can be added to the security baselines defined by Microsoft and applied immediately by the customer. Furthermore, IIJ Support optimizes these policies according to the customer's use situation.
Initial Setup of Microsoft Defender for Endpoint
We provide support for the onboarding to devices, alert notification settings, automatic response condition settings, and so on, necessary to use the EDR function. When this solution is used in conjunction with the IIJ C-SOC Service, we also perform the linking work.
Implementation of time-consuming operation verification on behalf of the customer
In addition to operation verification of policy content, IIJ also verifies the operation of highly useful new features released by Microsoft Intune and Defender for Endpoint. This greatly reduces the amount of work that must be performed by the customer and allows the full utilization of the features of Microsoft Intune and Defender for Endpoint.
Furthermore, if you have requirements beyond our predefined selections, we conduct operation verification based on your specific needs.
Ticket-based, simple & inexpensive fee structure
This allows for simple and easy-to-understand Microsoft Intune and Defender for Endpoint operations.
(Japanese text only)
- Related Contents
End of the page.