Top of Page
- Links to move inside this page.
- HOME
- IIJ Security Initiative
IIJ Security Initiative
Malware countermeasure based on DNS filtering
Updated September 24th,2019
As the Internet transforms into an indispensable part of social infrastructure like electricity and water, the number of connected devices has increased due to trends such as the Internet of Things (IoT), leading to a dramatic rise in traffic volume. But this has also resulted in more large-scale DDoS attacks that exploit vulnerabilities in IoT devices such as routers and monitoring cameras, which are difficult to protect with existing antivirus countermeasures. Attacks are also expected to increase when the Tokyo Olympics are held in 2020, based on past experience in London and Rio de Janeiro.
It was in this context that Japan's Ministry of Internal Affairs and Communications held a "Study Group on Appropriate Measures to Respond to Cyber Attacks at Telecommunications Businesses" in order to organize the appropriate measures to take against cyberattacks at telecommunications businesses, such as blocking C&C servers using DNS (*1). Further, in 2018, the Telecommunications Business Act and the Act on the National Institute of Information and Communications Technology (NICT) were amended to promote the sharing of information between telecommunications businesses, the blocking of malware infected devices and providing alerts for devices that may be infected with malware.
In 2016, IIJ built information analysis infrastructure based on big data security analysis and started implementing independent countermeasures to restrict malicious communication such as malware infection. After obtaining the consent of customers, the logs of subscribing customers are analyzed from a wide range of perspectives and reputation data (*2) is generated to enable malicious communication to be blocked. This malware countermeasure initiative is based on DNS filtering. When the DNS server you are using in an access service sends a name resolution request to a C&C server, malicious communication is blocked if the destination matches the reputation data. In this initiative, the logs for your DNS and related communication will also be used for customer support, and statistics and disclosing reports, as well as analysis to generate and improve the quality of reputation data.
We ask our customers to understand this IIJ initiative and to give your consent when using this service for us to perform DNS filtering and the analysis of DNS and related communication logs. Customers who do not want to give their consent may indicate their non-consent (opt out) to select that DNS filtering and analysis of DNS and related communication logs are not performed. This may be selected at any time. For details on the target services of this initiative and how to indicate non-consent (opt out), refer to "DNS filtering" and "Indicating non-consent (opt out)".
- (*1)An abbreviation of Command & Control server, this is a server that commands and controls devices infected with malware
- (*2)Address information for C&C servers generated by IIJ
Image of DNS filtering
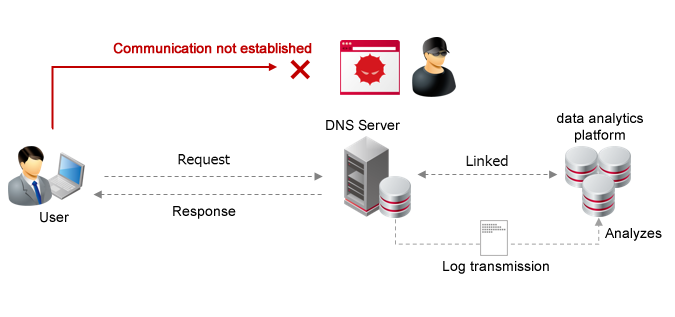
DNS filtering
| Item | Description | ||
|---|---|---|---|
| Overview | In the following target services, reputation data is input into the DNS server provided by IIJ, addresses matching the data are filtered (blocked), and the corresponding DNS and related communication logs are used for analysis and statistics and disclosing reports. Analysis starts from one month before the start of filtering application. | ||
| Cost | Free | ||
| Target service and filtering application start date (planned) | Dedicated line broadband access |
|
Planned Application starts from December 2, 2019 (Planned log analysis for advance evaluation starts from November 1, 2019)
|
|
Application starts from July 1, 2019 (log analysis for advance evaluation starts from June 3, 2019) | ||
| Mobile |
|
||
| Cloud |
|
Planned Application starts from December 2, 2019 (Planned log analysis for advance evaluation starts from November 1, 2019)
| |
| Individual | Visit the IIJmio website for information | ||
| Other services | We also plan to expand the scope to services other than those described above. When target services are added, information will be posted on the website and Service Online | ||
Details of consent
When using a service subject to this initiative, we ask that you consent to the following regarding the DNS server used in the service.
- Implementation of malware countermeasures based on DNS filtering for communication that matches the reputation data
- Analysis of DNS and related communication logs DNS
If you consent, you do not need to take any special action. IIJ will configure the applicable settings from the filtering application start date. If you do not give your consent, your use of the service will not be affected; however, please take note of the information in the following table.
| Item | Consent given | Consent not given |
|---|---|---|
| Required work | No work is required on the customer side. | The setting must be changed for the DNS server to which filtering will not be applied, and in the case of mobile, non-consent (opt out) must be indicated in Service Online. |
| Response to threats | Damage can be limited by blocking the communication of C&C servers or other devices that match the reputation data. | If communication occurs with a C&C server or other device infected with malware, communication may be established with other devices on which countermeasures are not applied. |
| Log analysis | The DNS and related communication logs are used for customer support, and for analysis to generate and improve the quality of reputation data. | The DNS and related communication logs are not analyzed. |
| Effect on current service | Multiple methods such as visual checks and periodic database updates are used to minimize effects caused by false positives or other issues. | No effects due to this initiative. |
Indicating non-consent (opt out)
Customers using dedicated lines, broadband access or cloud
The opt out is recognized when the customer changes the setting to a DNS server to which filtering is not applied. DNS servers without filtering applied can already be used. Refer below for the DNS server information and how to change the setting.
- General IIJ Services: "Notices" in Service Online
 (Japanese Text Only)
(Japanese Text Only) - IIJ GIO Component Service:"Notices" in IIJ GIO Support Web
 (Japanese Text Only)
(Japanese Text Only) - LaIT: LaIT Support Center
 (Japanese Text Only)
(Japanese Text Only)
ustomers using mobile
Set the opt out in Service Online. Refer below for how to opt out. Set the opt out in Service Online. Refer below for how to opt out.
- Mobile: "Notices" in Service Online
 (Japanese Text Only)
(Japanese Text Only)
Contact information
Corporate customers
IIJ DNS filtering support operating hours: 9:30 to 17:30 (closed on weekends and national holidays)
E-Mail: request-security@iij.ad.jp
- (*)In principle, only contact by email is accepted.
Individual customers
Telephone support: 0570-09-4400 (year-round, 9:00 to 19:00)
- (*)IIJ Support Center is available in Japanese only.
- (*)You may be asked for your name and mioID when making the inquiry.
End of the page.
